File Organisation and Encryption Program
HOME SOFTWARE FEATURES

LEARN ABOUT OUR NEW
GDPR File Organisation and Encryption Program
ADMINISTRATIVE AUDIT
The administrator overseeing the user account management can view the Audit Log of file actions. The Audit Log events include file viewing, sharing, exporting and more.
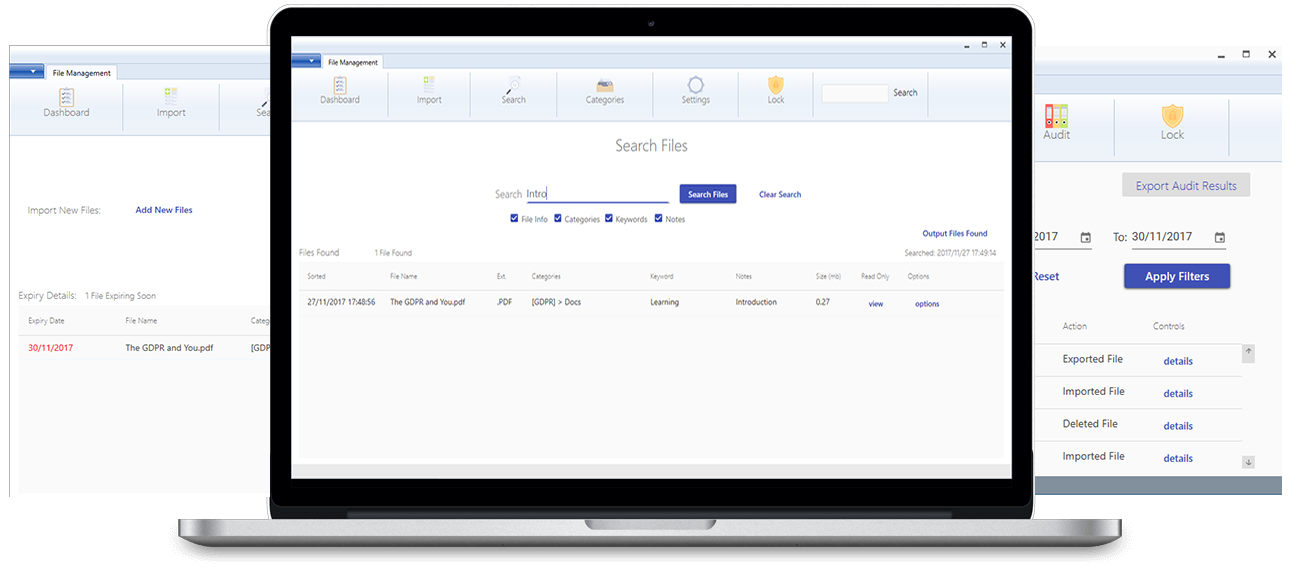
SEARCH & EXPORT
Secured Files can be searched based on attributes including categories, note and keywords. These files can be exported as a group or as individual password protected encrypted files for sharing with a third party.
EXPIRY HANDLING
There may exist a requirement for file removal after a certain period of time, our solution facilitates this expiry monitoring, giving the user the option of removal after the time has elapsed.
How Our GDPR File Encryption & Management Software helps
Encryption couldn’t be easier, all that is required is to simply save your files and documents through the ProtectorApp Encryption Program to encrypt and organise them in whatever filing system you wish to implement.
Benefits of this software
- It provides each organisation with an individualised encryption key, and a standalone secure encryption file environment.
- It provides a file protection solution to encrypt and secures data and files names (GDPR Art. 32.1(a))
- It provides file organisation through file categorisation, file sub-categorisation,
- It allows the additional filing capabilities through keywords, and notes.
- It allows the allocation of a file expiry date,
- It provides a search facility,
- It allows encrypted file sharing,
- It allows the exporting of password protected encrypted files,
- It provides a file expiry management system,
- It provides audit logs to record file activities and enhance security of data,
- It provides an auto logout features for added security.
- This encryption program allows organisations to choose the location where their data stored.
- It encrypts all files and file organizational structures to the highest encryption standards available (AES 256)
- The encrypted data is protected and is not accessible without the organisation’s encryption key protocol, which is unique to each organisation.
- It provides an audit trail in relation to file access and actions (GDPR Art. 32.4)
- It provides the capabilities of full event logging if required.
- It provides you with complete control of your data.
- Administrator(s) can access all audit logs.
- The application does not require internet connections to operate.
- It adds confidentiality and integrity to the processing systems – (GDPR Art. 32.1(b))
- It aids the assessment of the security level of the processing system – (GDPR Art. 32.2)
- It helps avoid serious heavy financial penalties – (GDPR Art. 83)
- It reduces the need to inform customers of encrypted data breaches – (GDPR Art. 34.3)
- It reduces the possibilities of any damage to the business reputation, possibilities of litigation, brand damage, loss of customers, loss of business,
- It reduces any loss of time as a result of the necessity for investigations surrounding breaches of non-encrypted data,
- It reduces the risk of bad publicity,
- It reduces the unwanted attention of the Data protection Commissioner’s office.
Protectorate Solutions Ltd., provides an encryption programming service that provides the highest standards of encryption, commercially available, through a user-friendly interface, which requires minimum training for its immediate use.
File Organisation and Encryption Program
We have developed a File Organization and Encryption Program which encrypts, organises and enables encrypted file sharing within a user group or to an individual. It provides your organisation with a unique encrypted key, making it a standalone secure and encrypted environment to protect your Personal Data. This program has been designed specifically for the requirements of the GDPR and the Data protection Acts, and it provides the highest standards of encryption commercially available through a user-friendly interface which requires minimum training for its use.
Our solutions are designed to provide you with absolute control and security over your data. No hosting account is required, your data may remain with you. This means you gain control of your data hosting along with processing capabilities, helping you to meet your responsibilities as a data controller and reducing the risk of being held responsible for a third-party processor’s data breach.
ProtectorApp includes friendly licence expiry, which means even if your licence expires and you choose not to renew it, you still have access to all your files and the ability to export them, you only lose the ability to add more files and some of the more optional features.
ProtectorApp – Instructional Videos
ProtectorApp - Intuitive Design & Increased Control
SECURITY SOLUTIONS FOR BUSINESSES AND ORGANISATIONS WHERE THE SECURITY AND PROTECTION OF PERSONAL DATA IS OF THE UTMOST IMPORTANCE.
File Sharing & Expiry Handling
It allows users to share access and leave comments / notes on shared files. It also allows users to set an expiry date on files giving the user the option of removal after the time it has elapsed.
File Searching & Categorisation
Each user can categorise their files to their own organisational structures and files can be searched based on attributes including categories, note and keywords. All of which are encrypted, increasing your data security.
Easy To Use
Our software is designed to be very user friendly, easy to set up and configure. It is very friendly towards non technical users, while still maintaining the level of security required.
Secure File Exporting Options
Files can be exported as a group or as individual password protected encrypted files for sharing with a third party.
Well Documented
Our solutions come with friendly user guides, including pictures and videos, to help users of all levels and backgrounds acclimate to their new system.
Audit Logs
The administrator overseeing the user account management has access to an Audit Log of file activities. The Audit Log events include file viewing, sharing, exporting and more.
The protection and secure access of your data is always our priority. If you would like further details and/ or a free trial version of the software please feel free to request one in the form below, we look forward to hearing from you!


